Welcome To
Unlocking The Secrets Of Digital Safety
Empower Your Cyber Journey

Welcome To My Domain
Find out more about my projects
Welcome to my Cybersecurity and Ethical Hacking lab. Here, you will find comprehensive IT security projects, hacking techniques, research, and more. This is my personal cyberspace, where I share write-ups for CTF challenges, articles about specific topics, and notes that might help others.
Latest Blog Posts
Cyber security is ever-changing, and choosing the best OS with the right toolkit is crucial for ethical hackers and security...
Virtualization software, such as VMware, Virtualbox, or Parallels, is the answer if you want to use many different operating systems...
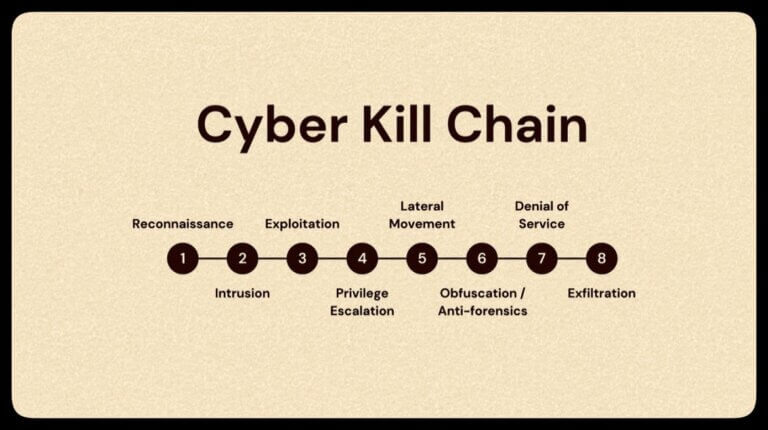
What is the Cyber Kill Chain in cyber security? Investing in cybersecurity analysis and strategy has never been more important...
The threat of Malware in Cybersecurity: Understanding the Risks This study aims to review and discuss the structure and overall...
AI is a Game Changer for Search Engines and SEO Future As digital gatekeepers, search engines like Google and Bing...
Cybersecurity is a broad topic that encompasses a large area within the IT security field. I published a short but...
Cyber-attacks, malware, and aspects of ransomware Cyber-attack stories and data breaches are becoming common, and perpetrators are more skilled and...
Caido- A lightweight web security auditing toolkit Caido is a new lightweight web security auditing toolkit designed to make professional-grade...
Using Google for Advanced Searching What is Google Dorking? Google has a lot of websites that have been crawled and...
How to find and exploit IDOR vulnerabilities in a web application giving you access to data you shouldn’t have...
Is a worm a virus? The answer is No. A worm is not a virus, although, like a virus, it...
1. Malware End devices such as computers, phones, tablets, and printers are particularly vulnerable to malware attacks. Therefore, this...
The difference between them What is a hacker? The term ‘hacker’ does not necessarily have a negative connotation. For the...
This is how to comply with the new EU regulation. Digital Operational Resilience Act The Digital Operational Resilience Act (DORA)...
This is What Happened. Quantum computers use quantum physics to access computational abilities that are different from classical computers...
A quick Google search for an answer will return many variations. Some will make sense to you, and some will...
Jepp, you are correct. A quick Google search for your data backup will give you 49 million results. You will...