What is the Cyber Kill Chain in cyber security?
Investing in cybersecurity analysis and strategy has never been more important in an era of rampant ransomware and other malicious cyberattacks.
The Cyber Kill Chain Explained
The cyber kill chain model is an adaptive, step-by-step process that helps organizations track, understand, anticipate, and stop cyber threats of all types. The term “cyber kill chain” comes from the military term “kill chain,” which refers to a series of stages or steps to prepare, attack, and destroy targets.
Two models, the Cyber Kill Chain (CKC) and the MITRE ATT&CK framework, can help security professionals harden network resources and protect against modern-day threats and attacks.
The CKC, developed by Lockheed Martin over a decade ago, provides a high-level view of a cyberattack’s sequence from initial reconnaissance through weaponization and action. While it is widely used by security teams, it has limitations. For example, host attack behaviors are not included in the model, and attackers may bypass or combine multiple steps.
The newer MITRE ATT&CK framework maps closely to the CKC but focuses more on cyber resilience to withstand emergent threats. This open-source project also provides substantial support for tracing host attack behaviors. The differences between the 2 models can have an outsized impact on the efficacy and resilience of the resulting security analysis and strategies.
The differences between the 2 models can have an outsized impact on the efficacy and resilience of the resulting security analysis and strategies.
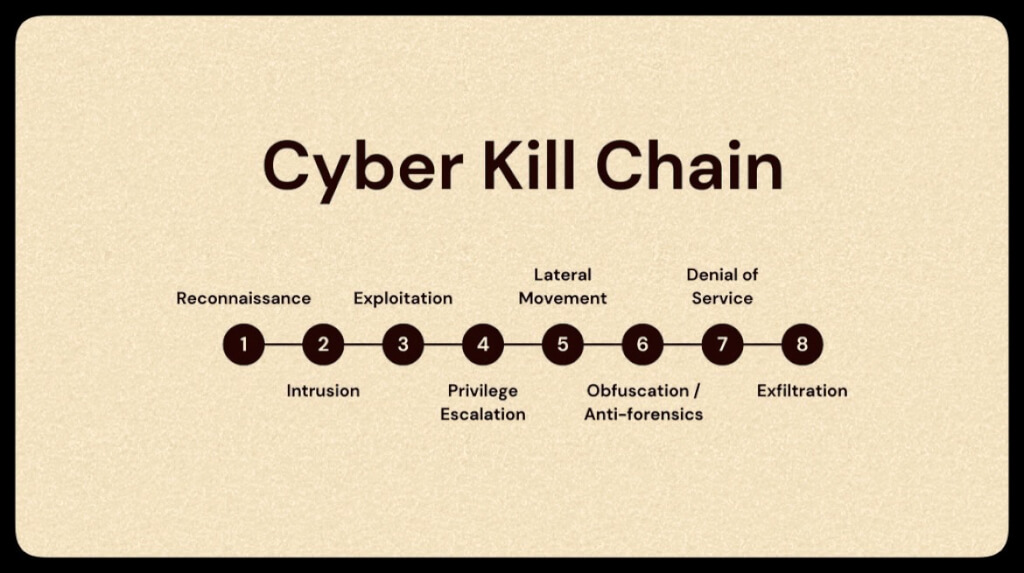
The Cyber Kill Chain typically consists of the following stages:
- Reconnaissance: Gathering information about the target. Vulnerabilities, email addresses, and other details are identified.
2. Weaponization: Creating or obtaining a malicious payload. A payload, such as a phishing email or other exploit, is constructed.
3. Delivery: Transmitting the payload to the target. The payload is delivered to targets identified during reconnaissance.
4. Exploitation: Taking advantage of vulnerabilities to execute the payload. Vulnerable devices or users inadvertently execute the payload.
5. Installation: An attack vector is installed on the victim’s system, and malicious software is installed to continue the attack’s execution.
6. Command & Control (C2): Establishing communication with the compromised system. The malware sends covert communications to the C&C servers, allowing the attacker to control compromised assets.
7. Actions on Objectives: The malicious software achieves the attacker’s ultimate goal by carrying out further actions via the C&C servers per the attacker’s instruction.

These 7 phases abstract and simplify attack behaviors, allowing security teams to categorize them by stages rather than analyzing and defending against individual behaviors.
A typical process for analyzing and mitigating attacks under the CKC model includes the following:
Mapping attack behaviors into kill chain stages and understanding the behaviors based on descriptions of the stages
Initiating detection and mitigation strategy for the attack behaviors as suggested by the corresponding kill chain stages
Prioritizing execution via detection and mitigation tasks. Prioritizing is crucial because security team resources are often limited.
The Value of Prevention
When performing security tasks, it is important to remember that prevention is better than detection. A prevention strategy aims to completely nullify an attack so that no residual damage is done to the systems and no cleanup is required. However, prevention is only possible under certain early-stage scenarios, such as during reconnaissance, delivery, and exploitation. At the installation and C&C stages, malware has already caused permanent modifications to systems, so prevention is no longer possible.


Thiago
Great article