How to find and exploit IDOR vulnerabilities in a web application giving you access to data you shouldn’t have.
What is an IDOR?
IDOR stands for Insecure Direct Object Reference and is a type of access control vulnerability. These types of vulnerabilities arrise from acces control issues. This can occur when a web server receives user-supplied input to retrieve objects such as files, data, or documents. Too much trust has been placed in the input data, and it is not validated on the server side to confirm that the requested object belongs to the user who ordered it.
What are insecure direct object references (IDOR)?
Insecure direct object references (IDOR) are access control vulnerabilities that occur when an application uses user-supplied input to access objects directly. IDOR gained attention when it appeared in the OWASP 2007 Top Ten, but it is just one example of access control implementation mistakes that can compromise security. IDOR vulnerabilities are often linked to privilege escalation.
IDOR examples
Many access control vulnerabilities exist where user-controlled parameter values are used to access resources or functions directly.
IDOR vulnerability with direct reference to database objects.
Consider a website that uses the following URL to access the customer account page by retrieving information from the back-end database:
https://insecure-website.com/customer_account?customer_number=132355
The customer number is a record index in queries performed on the back-end database. If no other controls are in place, an attacker can modify the customer_number value, bypassing access controls to view the records of different customers.
This is an example of an IDOR vulnerability leading to horizontal privilege escalation.
An attacker might be able to perform horizontal and vertical privilege escalation by altering the user to one with additional privileges while bypassing access controls.
Question
What does IDOR stand for?
> Insecure Direct Object Reference, you are right!
IDOR Example
Imagine if you’ve just signed up for an online service and want to change your profile information. The link you click on goes to http://online-service.thm/profile?user_id=1305, where you can see your information.
Curiosity gets the better of you, and you try changing the user_id value to 1000 instead (http://online-service.thm/profile?user_id=1000), and to your surprise, you can now see another user’s information.
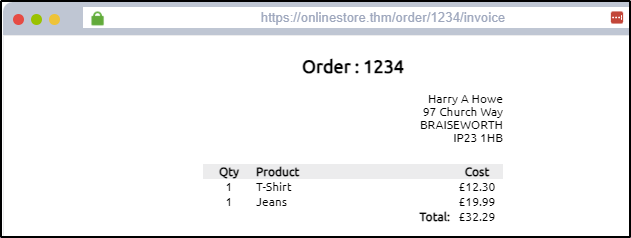
Look at the link above and test our curiosity by changing the order ID from 1234 to 1000.
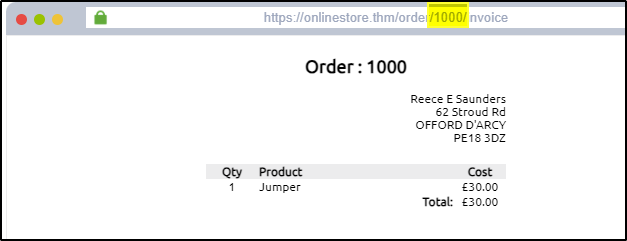
Changing the order ID from 1234 to 1000 has displayed another user’s invoice, confirming an IDOR vulnerability on the website. Ideally, the website should be checked to verify that the user information belongs to the user who logged in and requested it.
🚩The Flag from the IDOR example is:

Finding IDORs in Encoded IDs
Encoding IDs
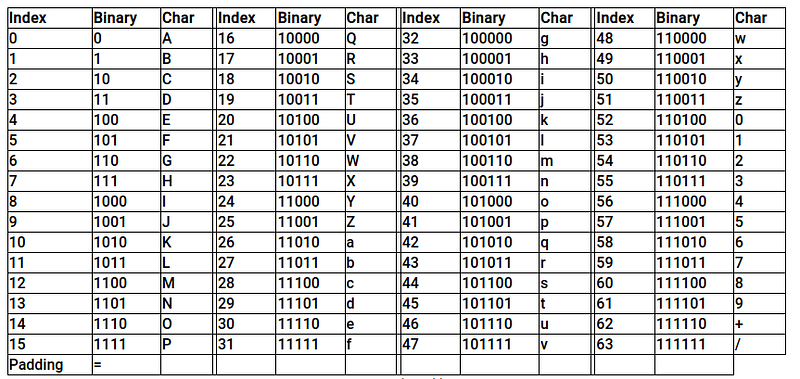
Web developers often first encode the raw data when passing data from one page to another, either by post data, query strings, or cookies. Encoding ensures that the receiving web server can understand the contents. Encoding changes binary data into an ASCII string, commonly encoding method using the a-z, A-Z, 0–9, and + and / = characters for padding.
The most common encoding technique on the web is base64 encoding, which is usually pretty easy to spot. As per the base64 representation table, the binary data can be converted to 64 different ASCII characters — which are easy to transmit and printable.
A total of 64 ASCII characters to represent binary from 000000 to 111111. Each non-final Base64 digit represents exactly 6 bits of data.
Bash base 64 encode and decode
Basic syntax
base 64 [options] [INFILE] [OUTFILE]
Option: You can provide any options or combine them as explained below.
INFILE: Input can be picked up from standard input (command line or files).
OUTFILE: You can redirect the output to the standard output (terminal or a file).
How to Encode Data with Base64 in Python
In Python, you can use the built-in Base64 Python standard package.
1.Import the library inside your Python file by using this command:
import base64
2. Then use the base64.b64encode() function to encode a string into Base64 encoded ASCII characters. We’re using “Hello’” for this example.
encoded = base64.b64encode(b'Hello')
3. Print out the result to see what “Hello” looks like in Base64 format.
print(encoded)

How to Encode & Decode with Base64 in Linux
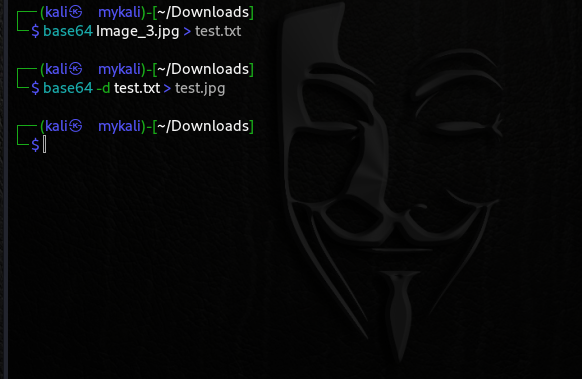
Every Linux distribution comes with a Base64 encoding and decoding utility. To convert an image using base64 encoding, append the image path after the base64 command.
base64 Image_3.jpg
Or you can save the output base64 encoded ASCII to a .txt file as such:
base64 Image_3.jpg > test.txt
You can use websites like https://www.base64decode.org/ to decode the string, edit the data, re-encode it using https://www.base64encode.org/, and resubmit the web request to see if the response changes.

Question
What is a common type of encoding used by websites?
> base64, you are right!
Finding IDORs in Hashed IDs
Hashed IDs
Hashed IDs are slightly more complicated than encoded ones, but they may follow a predictable pattern, such as being the hashed version of the integer value. For example, ID 123 would become 202cb962ac59075b964b07152d234b70 if MD5 (message-digest algorithm)hashing were used.
It’s worthwhile putting any discovered hashes through a web service such as https://crackstation.net/ (a database with billions of hash values) to find matches.
Question
What is a common algorithm used for hashing IDs?
> md5, you are right!
Finding IDORs in Unpredictable IDs
Unpredictable IDs
If the ID cannot be detected using the above methods, an excellent method of IDOR detection is to create two accounts and swap the ID numbers between them. If you can view the other users’ content using their ID number while still being logged in with a different account (or not logged in at all), you’ve found a valid IDOR vulnerability.
Question
What is the minimum nr. of accounts you must create to check for IDORs between accounts?
> Two, you are right!
Where are IDORs located?
Where are they located?
The vulnerable endpoint you target may not always be visible in the address bar. Content could be loaded via an AJAX request or referenced in a JavaScript file.
Endpoints in production may contain unreferenced parameters, such as a user_id in /user/details?user_id=123, which could be exploited through parameter mining to access other users’ information.
A Practical IDOR Example
I will conclude this article with a practical IDOR example.
For testing purposes, I’ll use this link: https://10-10-134-181.p.thmlabs.com. First, we need to create an account.
The account section allows you to change your information, such as username, email address, and password. The username and email fields are pre-filled in with your information.
We’ll start by investigating how this information gets pre-filled. If you open your browser developer tools, select the network tab, and then refresh the page, you’ll see a call to an endpoint with the path /api/v1/customer?id={user_id}.
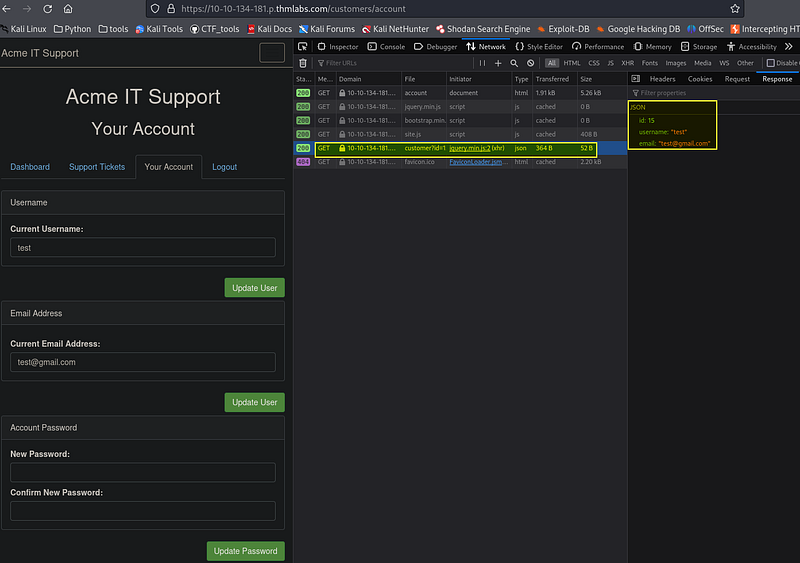
This page returns your user ID, username, and email address in JSON format. The path shows that the user information is taken from the query string’s id parameter (see below image).

You can test this ID parameter for an IDOR vulnerability by changing the ID to another user’s ID. Try selecting users with IDs 1 and up to 11.
And there, we have the credentials for another user.
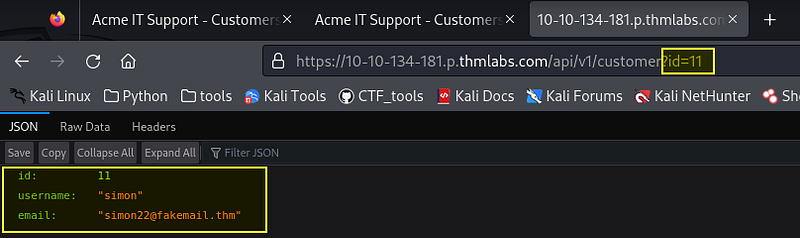
If you are still tinkering with the user_id, you will eventually find the correct username and password.
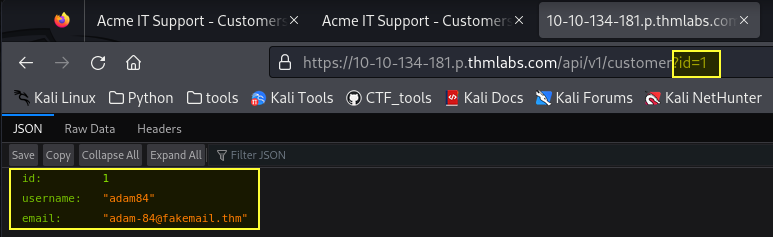
Good job making it this far! In this particular case, it happens to be user id 1.
user id 1 = adam 84
user id 3 = [email protected]
Thank you for visiting my blog.
CyberLuk3