If you’re seriously involved in cybersecurity or digital forensics, you’ve likely
encountered a variety of appropriate tools designed to address common challenges within these fields.
These tools are essential for threat detection, incident response, data recovery, and investigative analysis. They provide professionals with the resources to protect systems and recover evidence efficiently.
In this post, I will discuss Cyberchef, the Cyber Swiss Army Knife — a web app for encryption, encoding, compression, and data analysis.
The British government provided Cyberchef, more precisely, the GCHQ, the global communication headquarters. So, this service is part of the British intelligence MI5 and MI6.
They have made it available on Github for everyone to use. You may run this tool on your browser or download it and run it on your local machine.

If you want the tool to be portable, you can also download it and copy it to a pen drive.
This excellent tool has over two hundred functions, organized in section 3, “Operations,” on the left side.
It works based on the operation you want it to perform, either encryption, decryption, or encode/decode.
Let’s say you want to obfuscate plain text by encoding it to Base64. You will copy and paste your input in the “1 “field in the top right corner and then from favorites categories with the drag/drop “to Base64” function into Recipe “4” as such.
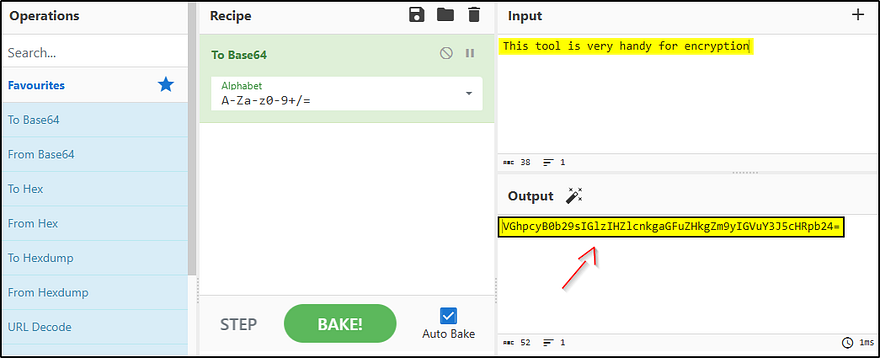
Once you enter the input and the desired encoding/encryption function, you can “bake” the recipe. Alternatively, it will do it automatically, as shown above.
To complicate the output further, you can add another function to a HEX value, for instance.
To decode the output, you must do the exact process but backward. So, let’s delete all the input and clear our recipe platform.
To test the decoding process, copy the Hex result from the output and paste it into the input.
Now, let’s try something else. When you upload an image, you can resize it, change its format, invert it, flip it, and the list goes on and on.
As shown above, we uploaded an image and added three different functions.
#1. The first one was to invert the image (the colors would then be reddish), but then I changed my mind and decided to disable the function without removing it.
#2. The second function I added was to flip the image horizontally, and as shown, the penguin is now looking at the right side.
#3. The third function added was to blur the image; our tool did just that.
There are many options, and this is a must-have security tool often used by cybersecurity and forensics experts.
Some of the most common (text-based) encoding formats you may encounter in capturing the flags competitions, etc., are Base64, ROT13, and URL Encoding.
If you’d like to learn more about encoding and decoding, I’d like to challenge you to decode the following. Remember that you can use multiple functions.
VnMgbGJoIHl2eHIgemwgcGJhZ3JhZywgZmdubCBnaGFycSwgbmFxIGN5cm5mciBwYmFmdnFyZSBvaGx2YXQgenIgbiBwYnNzcnIuCkd1bmF4IGxiaCBzYmUgbGJoZSBmaGNjYmVnIQoKb2hsenJucGJzc3JyLnBiei95aHgzIA==
Thank you for reading. Stay tuned for more articles about cybersecurity, bug hunting, and encryption/decryption.