How to detect and exploit SQL Injection vulnerabilities.
Structured Query Language (SQL) Injection, or SQLi, is a web security vulnerability that allows an attacker to interfere with queries an application performs to its database.
This method will allow attackers to view data that is typically not accessible. This data may belong to other users or any other data that the application can access.
An attacker can often delete or modify this data, which may permanently alter the application’s behavior.
How to detect SQL injection vulnerabilities
SQL injection can detected manually by using a systematic set of tests against every entry point in the application.
For example, you can submit a quote” ‘ “ character and look for errors or misbehavior.
You may also use boolean conditions such as “OR 1=1” and “OR 1=2” to check how the application responds.
If you prefer using tools to find most SQL injection vulnerabilities, you can use Burp Scanner.
SQL injection in different parts of the query
Most SQL injection vulnerabilities occur within the “WHERE” clause of a “SELECT” query.
If you are familiar with SQL query language, you know what it means.
Most experienced testers know this type of injection well.
SQL injection can occur at any location within the query and different query types. You may find these in the “UPDATE,” “INSERT,” and “SELECT” statements within the “ORDER BY ”clause.
Retrieving hidden data
If you are using a shopping application that shows many products from different categories when the user chooses a category, let’s say Gifts, the URL in the browser will look like this:
https://insecure-website.com/products?category=Gifts
In this case, the application will make an SQL query to retrieve the details of “Gifts” from the database:
SELECT * FROM products WHERE category = 'Gifts' AND released = 1
What happens here is that the SQL query asks the database to return:
> all details (*)
> from the “products” table
> where the “category” is “Gifts”
> and “released” is 1
The restriction “released = 1” hides the unreleased products. If you change that parameter, the application may give us a different answer.
The application is not designed to implement any defenses against SQL injection attacks, and this means an attacker can construct an attack as such:
https://insecure-website.com/products?category=Gifts'--
In this case, the SQL query will look like this:
SELECT * FROM products WHERE category = 'Gifts'--' AND released = 1
It is imperative to note that “- -” is a comment indicator in SQL, meaning that the rest of the query is interpreted as a comment. The query no longer included the “AND released = 1”, and the application will display all products not yet released.
Another similar attack causes the application to show all the products in any category, even those that they don’t know about:
https://insecure-website.com/products?category=Gifts'+OR+1=1--
In this case, the SQL query will look like this:
SELECT * FROM products WHERE category = 'Gifts' OR 1=1--' AND released = 1
The query will return all the items where either the category is “Gifts”, or 1 is equal to 1. Since 1=1 is always true, and the query returns all items.
Let’s test the theory in a LAB environment.
Disclaimer: do not perform this type of attack without written authorization, or you can be sued.
Lab: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
To solve the lab, you must perform an SQL injection attack that causes the application to display one or more unreleased products.
https://web-security-academy.net/filter?category=Corporate+gifts
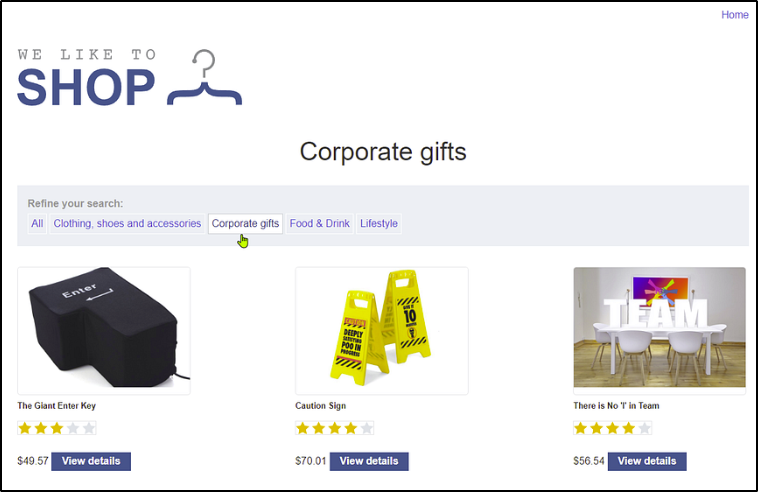
Accessing the corporate gifts from the webshop will trigger the application to perform an SQL query to the database.
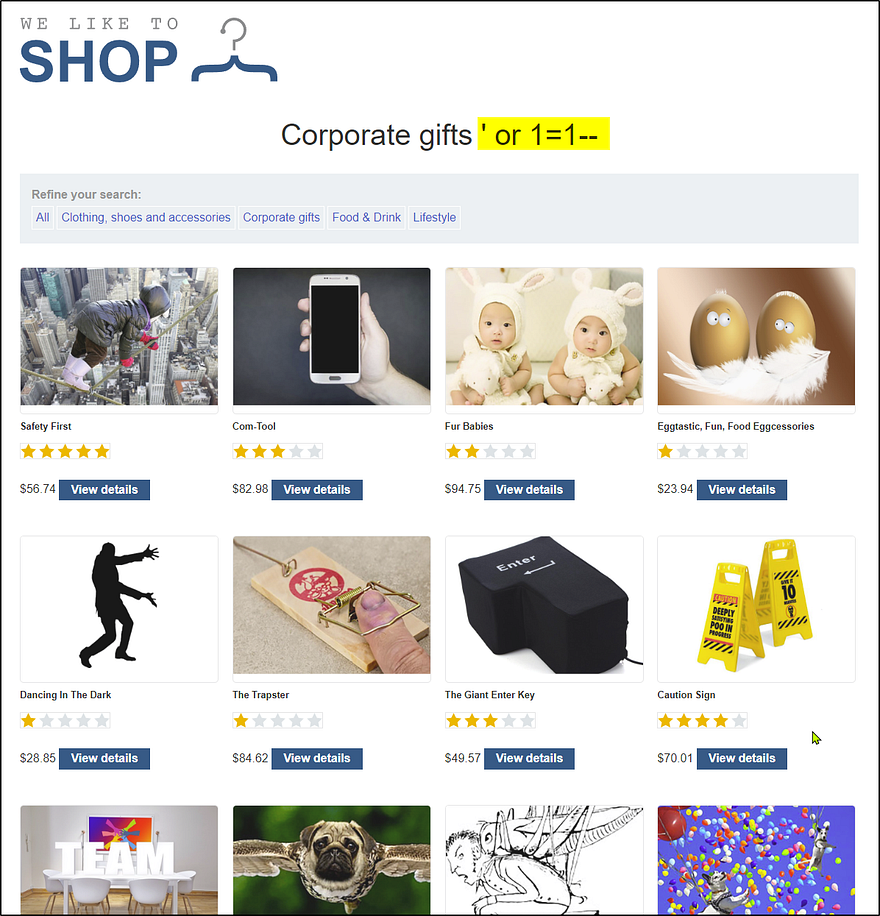
https://web-security-academy.net/filter?category=Corporate+gifts%20%27+or+1=1--
Tempering with the SQL query in the “WHERE” clause from the URL resulted in a successful attack, and we can see all the products, as explained above.

Well done!
Thank you for reading my blog post. Feel free to connect and subscribe for more content.